Ever wanted a simple tool capable of performing a side-channel attack of HTTP requests? A common use case would be to test of the login action takes more time of the provided username is known by the system compared to an unknown username. The theory behind such an attack is that the code performing the login stops more early in the flow if the used username is not present in the system.
Well, to test such a weakness it is necessary to perform certain HTTP requests, e.g. logins, and to capture the need time to receive a response. But what tools are fulfilling these requirements? The search can’t be this hard. In fact the most common web application penetration tool Burp Suite is in fact capable of this task. The following steps will demonstrate how to conduct a test for side-channel attacks.
- Select the Request to be analysed and send it to the intruder
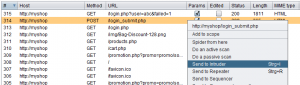
- In the Intruder Tab you have to select the Payload Position (marked with §§) you want to alternate, e.g. the username:
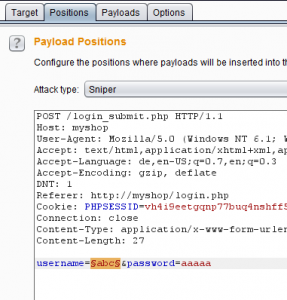
- Configure the rest of the Intruder Options as you like, while you at least have to choose a payload
- After this you can start the attack. The intruder will fire one http request for each configured payload item.
- The new window listing all issued requests has to be configured to list the time needed to receive the response:
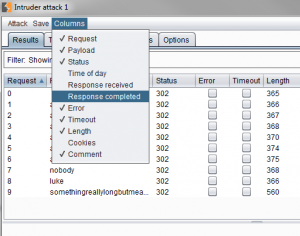
- With this extra column it is now possible to see if certain username influence the response time and if the login is vulnerable to a side-channel attack:
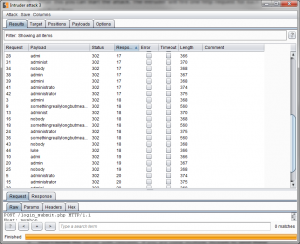
Important remark on those tests on HTTP traffic:
- At first it is recommended to send the same payload multiple times to verify that the measures time is reproducible.
- Don’t bomb the server with requests. If you are using multiple threads to send these requests, the server has to deal with all of them at the same time, which reduces the validity of the measurement. Leave the server enough time to recover from each request.
- The time to complete the response does not only depend on the code residing on the server but mostly on the route to the server and back. So most likely any measures done to remote servers are not representative as the network component has a much higher impact on the response time. The result is that all responses will take almost the same time to complete.
- Hooking Burp Suite in Client Software Communication - 6. July 2017
- PHP: Exploitation with $_REQUEST while validating $_GET - 20. May 2016
- HTTP Side-Channel Attacks with Burp Suite - 25. April 2016